Willkommen in der Prezi Galerie
Entdecken Sie die besten, von unseren Editoren zusammengestellten Prezi-Präsentationen und lassen Sie sich von ihnen inspirieren. Hier können Sie Präsentationsbeispiele für eine Vielzahl von Themen, aktuellen Ereignissen und Branchen finden.
#diversityandinclusion
Beliebte Kategorien
Schauen Sie sich die besten Videos aus den Top-Kategorien an
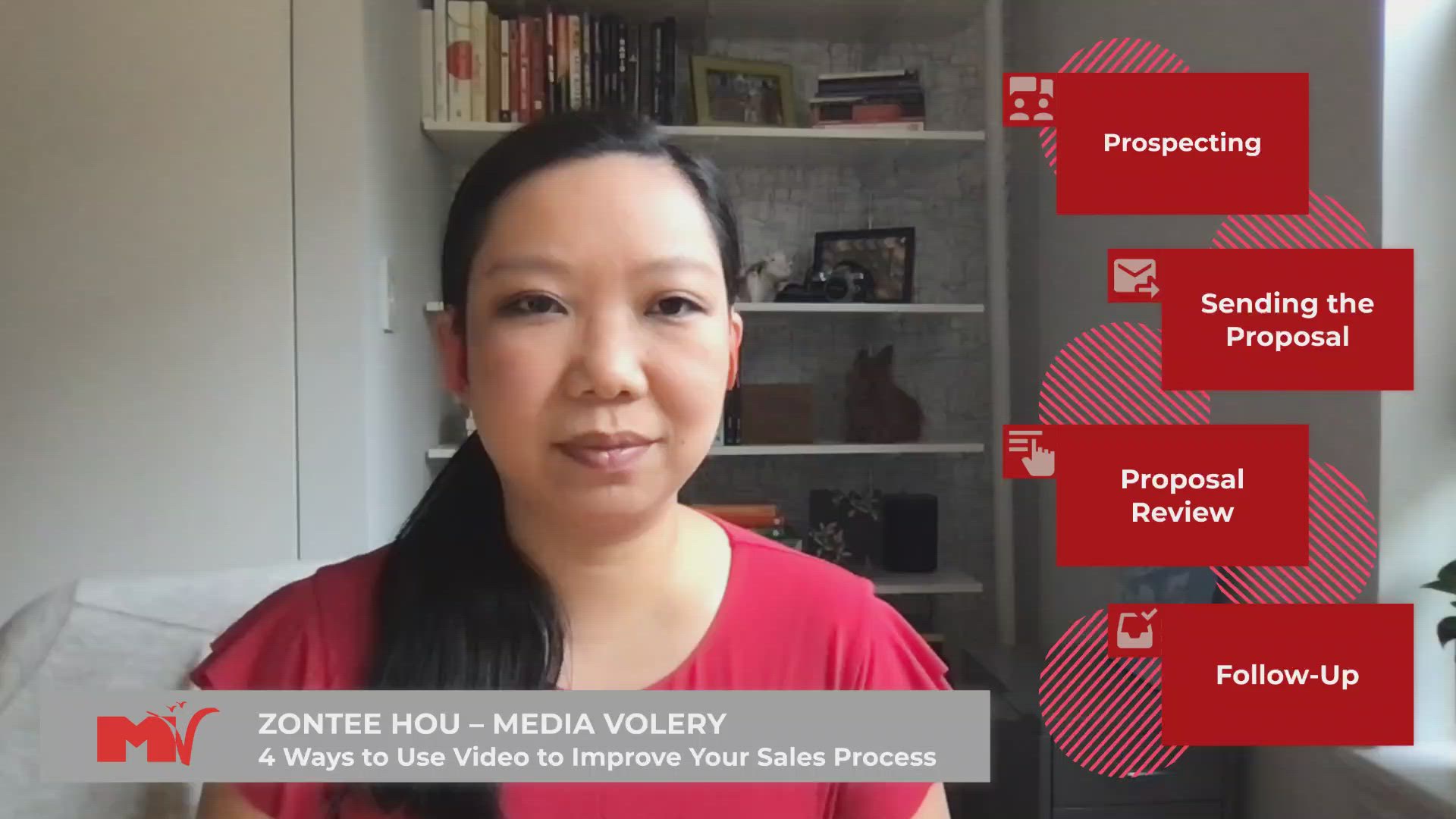
#VirtuelleSales
Schauen Sie sich an, wie diese Sales-Experten Ihnen dabei helfen können, Ihre virtuellen Sales auf das nächste Level zu bringen.
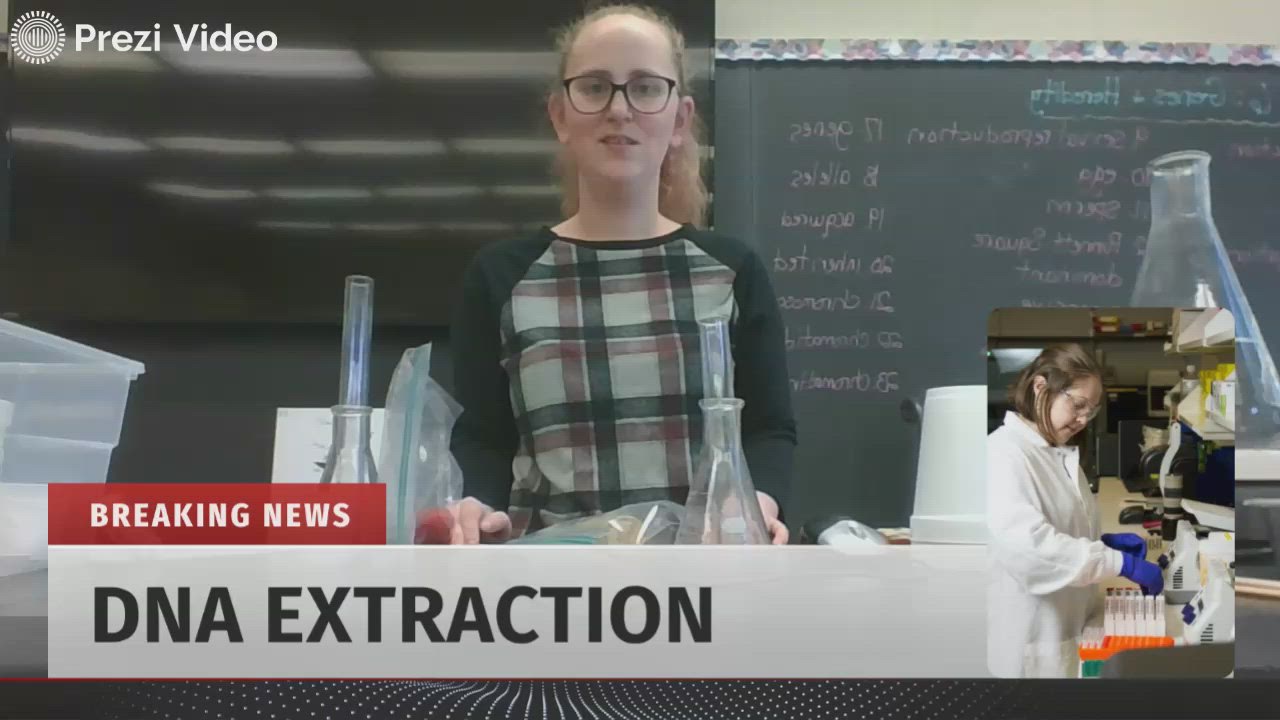
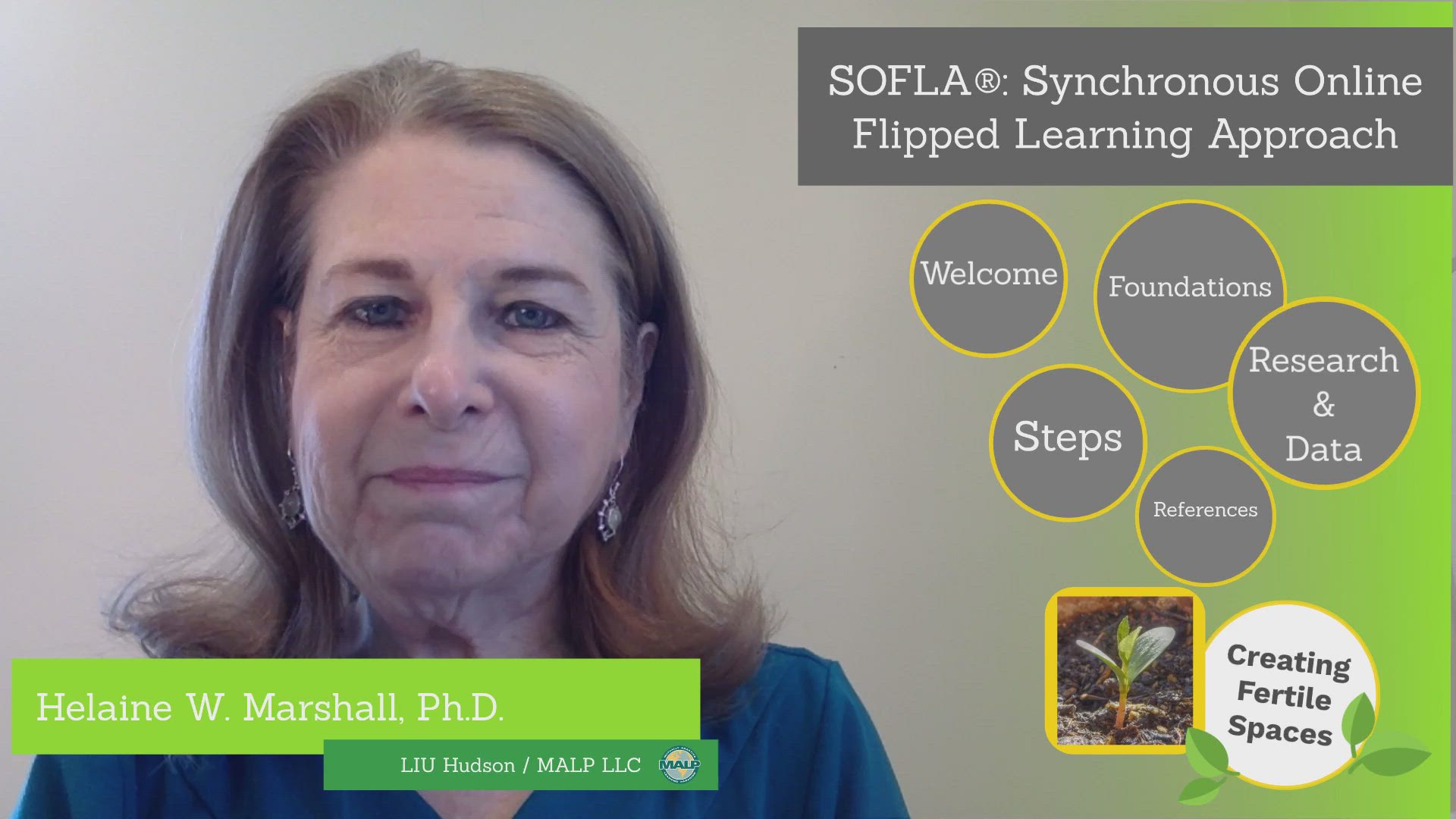
Alle Videos anschauen →#GemischtesLernen
Sehen Sie, wie Pädagogen Videos kreativ einsetzen, um das Lehren und Lernen im Internet zu unterstützen.
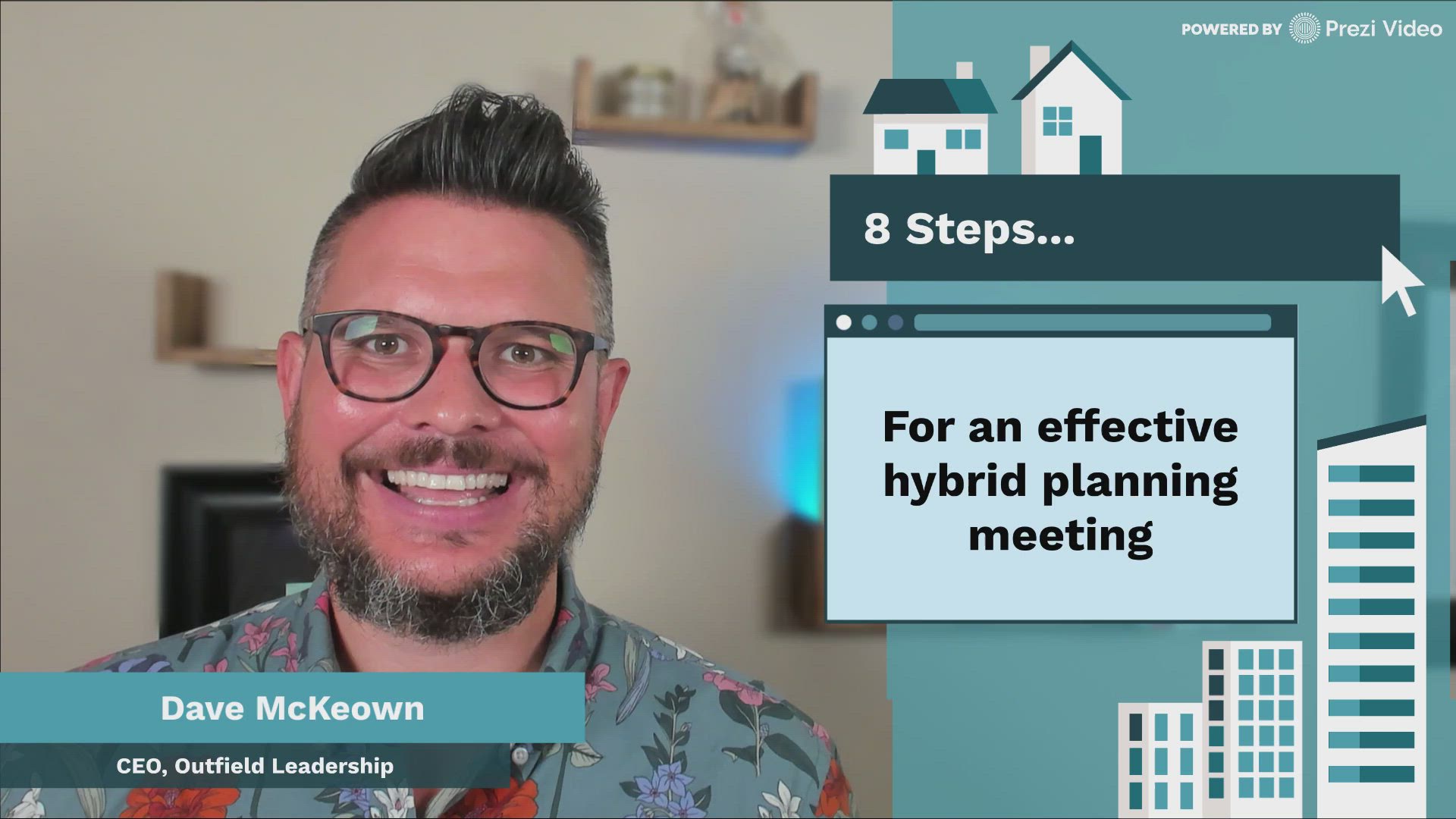
Alle Videos anschauen →#HybrideArbeit
Lernen Sie optimale Methoden und erhalten Sie Expertentipps zum Arbeiten von zu Hause.
Alle Videos anschauen →