1-844-773-9449
8:30 am–5 pm PST 태평양 표준시












이제 화상 통화 시 화면 공유로 내 얼굴을 가릴 필요가 없습니다. 시선이 집중되는 온라인 프레젠테이션, 데이터 중심의 보고서 등을 만들고, 화면에 나와 나의 컨텐츠를 함께 보여주어 더욱 기억에 남는 화상 통화 경험을 만들어보세요.
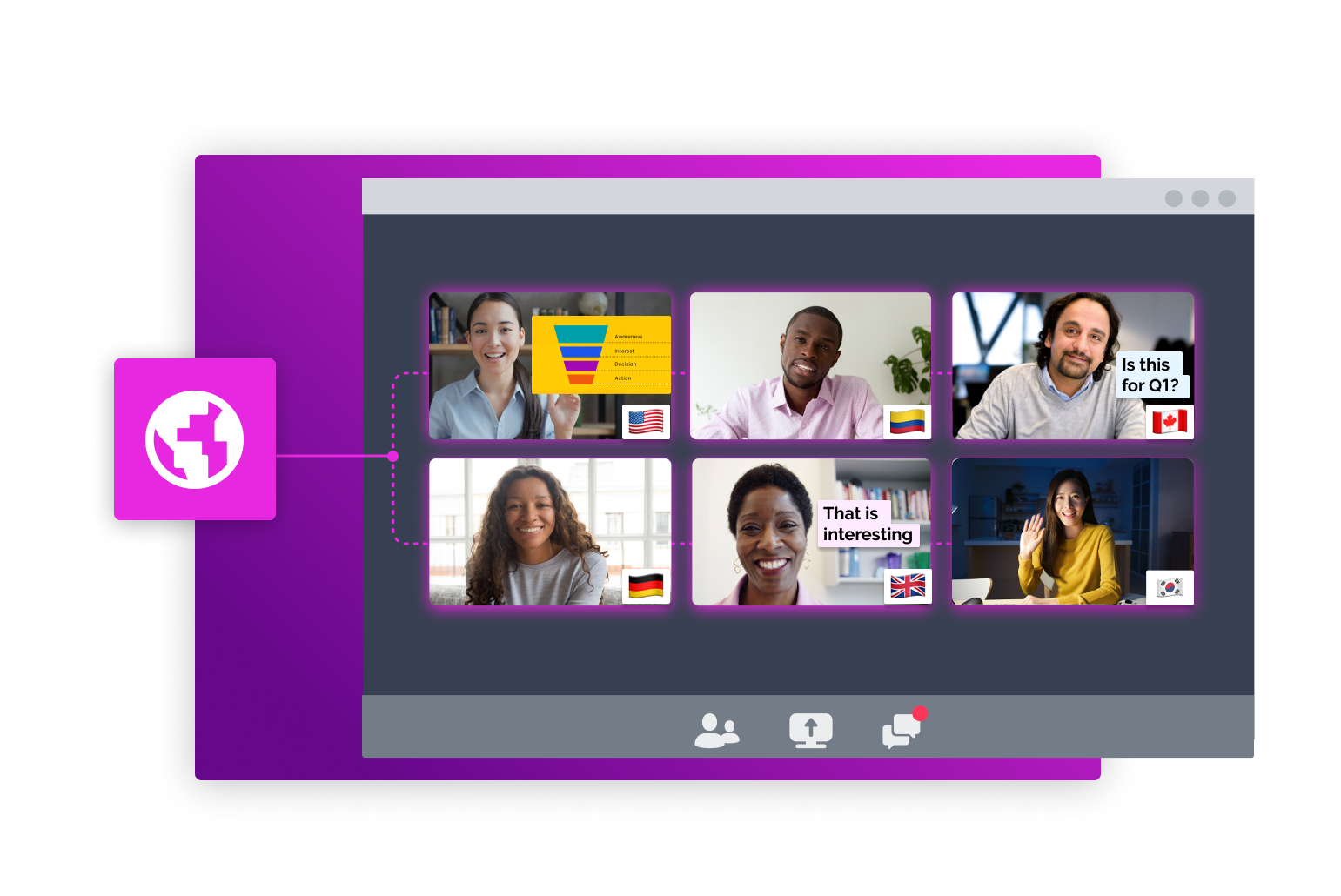
팀원 모두에게 흥미롭고 동등한 회의 경험을 만들어주세요. 재택 근무하는 팀원도 사무실에서 일하는 팀원도 모두 집중하는 온라인 프레젠테이션을 만들고 공유하세요. 더 많은 방법으로 참여하고 소통할 수 있어, 팀원 개개인은 어디에서 일해도 자유롭게 소통하고 아이디어를 공유할 수 있는 동등한 기회가 부여됩니다.
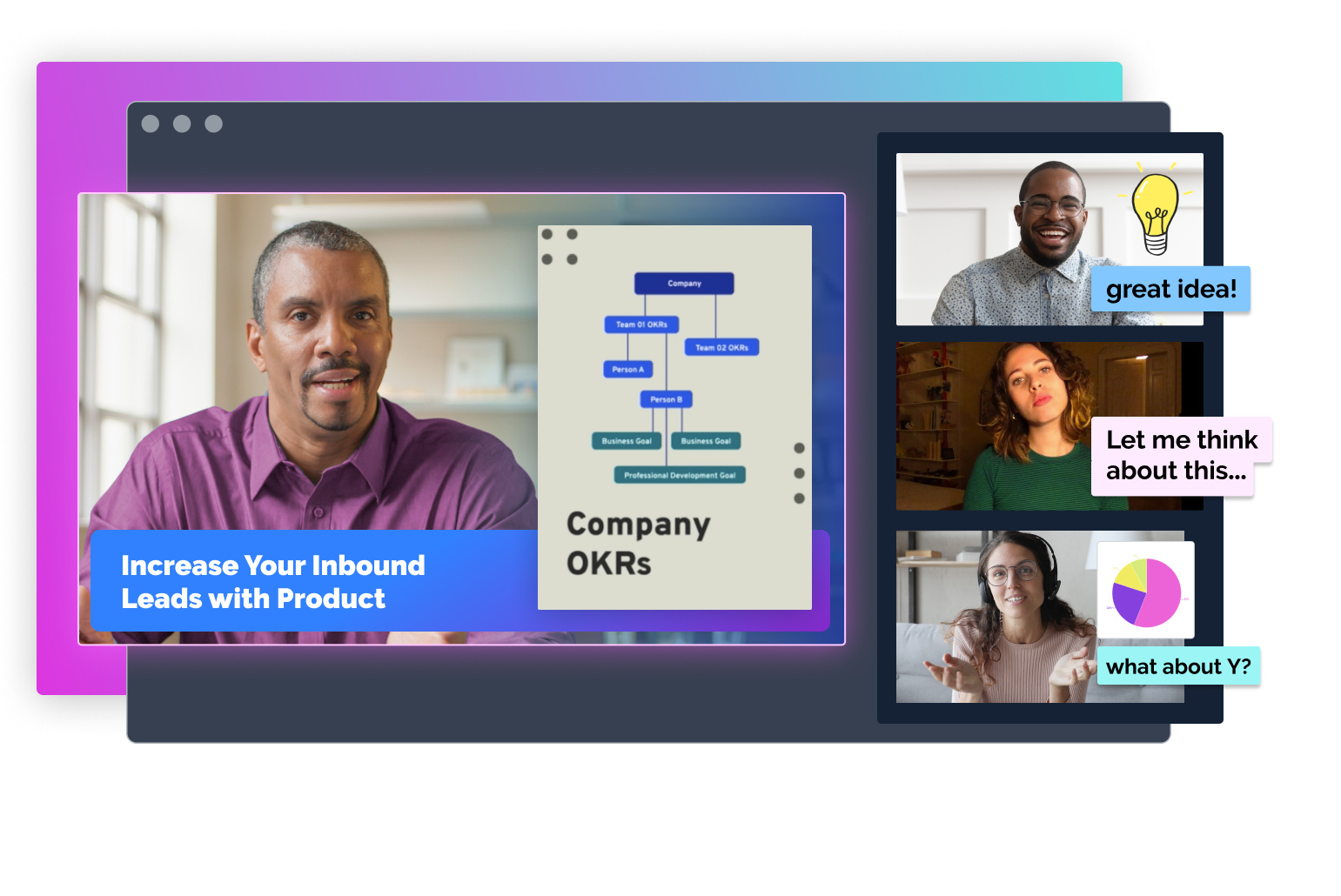
Prezi의 협업 기능으로 팀원 간의 대화와 소통을 늘리고 프로젝트 중간점검, 워크샵, 팀 회의의 생산성을 올려보세요. GIF와 댓글로 영상 회의 중 화면에 즉각 반응을 보일 수 있습니다. Prezi에서 공동 프로젝트를 만들어 공유하고, 댓글과 분석 툴로 팀워크를 강화하세요.
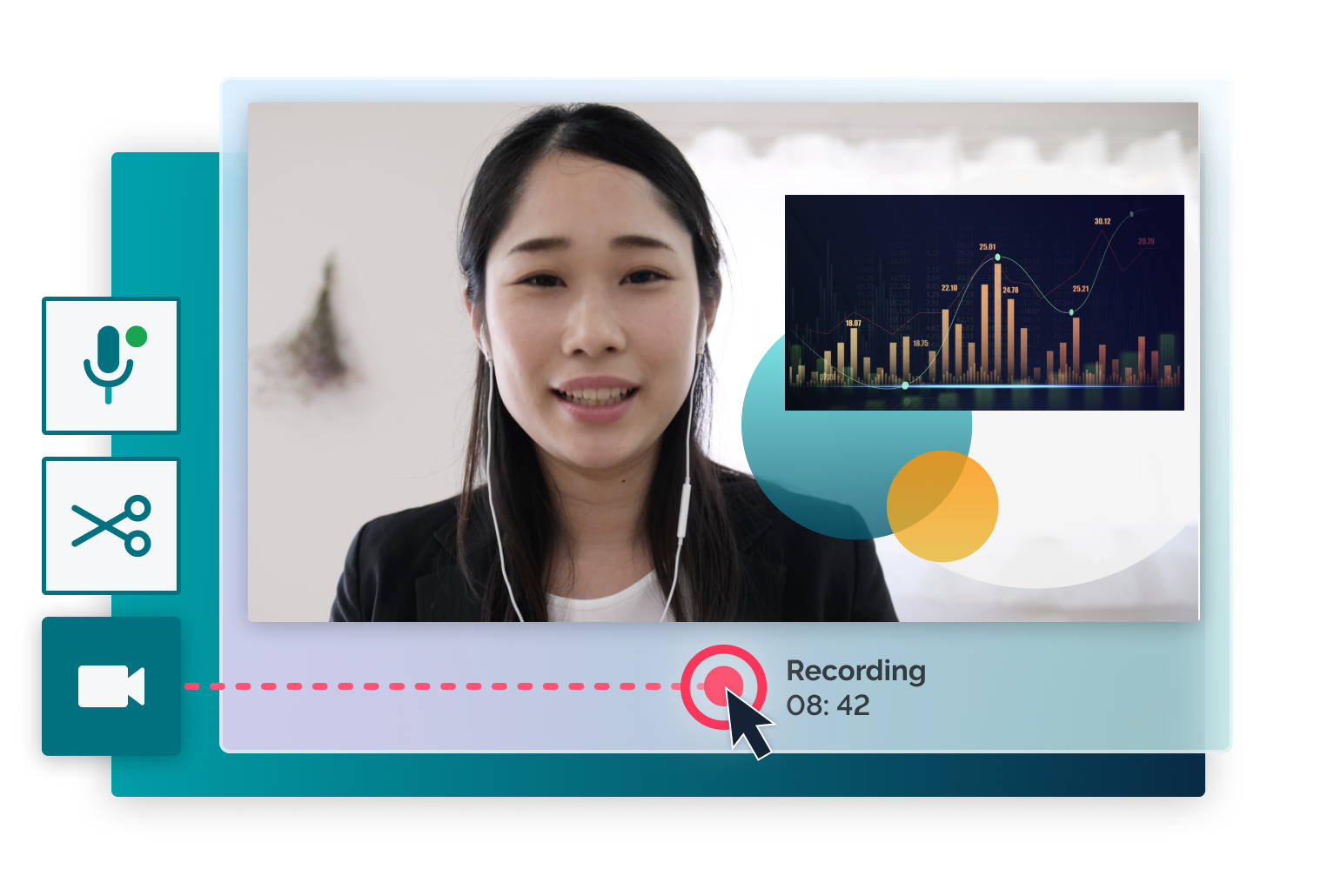
다양한 장소에 분산된 하이브리드 팀들과 더욱 흥미롭고 생산적인 회의를 하세요. 더욱 영향력있는 온라인 프레젠테이션을 만들고 Prezi Video로 팀과 영상 통화를 하며 프레젠테이션을 공유하세요. 회의에 참석할 수 없나요? 걱정 마세요. Prezi Video로 영상을 만들고, 마이크로소프트 팀즈, 슬랙 등의 메시지 앱이나 이메일로 공유하세요.
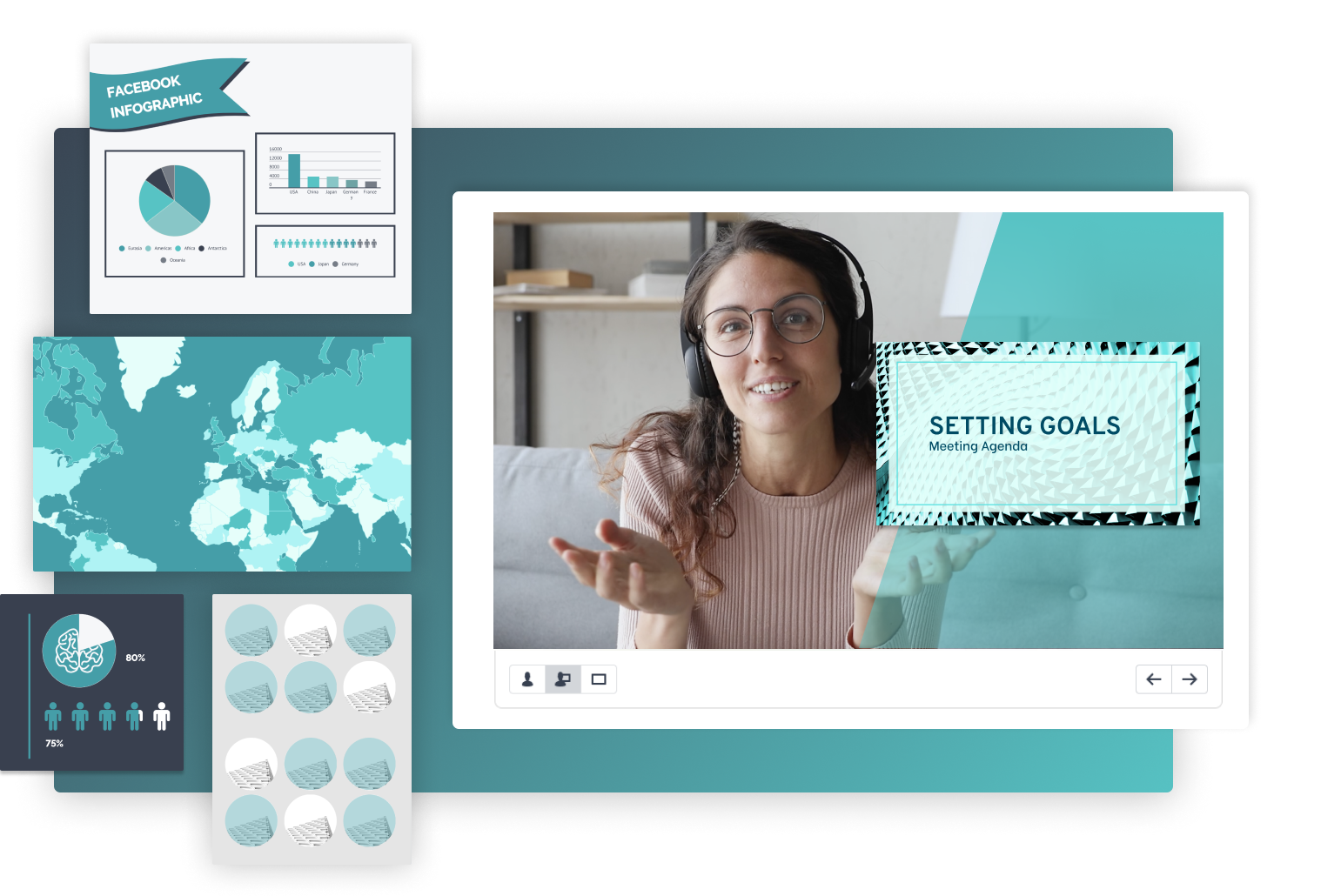
화면 배경부터 프레젠테이션 및 소셜미디어 컨텐츠까지 하이브리드 환경에서 다양한 시각 컨텐츠를 브랜드에 맞게 만드는 일은 중요합니다. 모두 Prezi로 만들어보세요.
Prezi 브랜드 키트에 대해 배우기Prezi Video와 자주 사용하시는 인기 영상 회의 앱을 쉽게 연결하여 청중의 집중력을 올려보세요.















라이센스 관리
팀원 추가 및 삭제, 라이센스 이전이 쉽습니다.

컨텐츠 소유권
팀의 컨텐츠를 관리할 수 있습니다. 심지어 팀원이 떠날 때에도.

공개범위 관리
공개 범위 설정으로 누가 무엇을 볼 수 있는지 자유롭게 설정할 수 있습니다.

MSI 설치
원격 소프트웨어 배포로 모두가 최신 버전을 빠르게 이용할 수 있습니다.


전화 및 채팅 지원
저희 고객지원 팀은 도움을 드리기 위해 상시 대기 중입니다.

전담 고객 관리자
전담 고객 관리자가 팀이 쉽고 빠르게 이용하실 수 있도록 도와 드립니다.

브랜드 템플릿
나의 브랜드에 맞는 폰트, 로고, 색상으로 구성된 템플릿을 이용하세요.

고급 사용법 강의*
맞춤형 사용법 강의 및 웨비나를 이용하고, 원하실 경우 Prezi 수료 인증서를 받으실 수 있습니다.
*소프트웨어 최소 이상 구매 시 해당


SOC2 규정 준수
저희는 SOC2 요구 사항을 준수하고 계속해서 규정에 맞게 업데이트하고 있습니다.

지속적인 모니터링 저희는 지속적으로 인프라와 앱을 면밀히 살펴보고 테스트하고 있습니다.

팀 통합 협업
저희 보안팀, 엔지니어팀, 제품팀은 서로 긴밀히 협업합니다.
저희 보안 대응에 대해 자세히 알아보세요
하이브리드 근무 환경은 직원이 사무실이나 온라인에서 일할 수 있는 유연함을 기본으로 합니다. 하이브리드 근무 모델은 다양한 형태로 존재합니다. 어떤 직원은 완벽히 사무실에서 일하고, 다른 직원 완벽히 온라인에서 일하기도하며, 또 다른 직원은 두 형태를 섞어 두 공간에서 일하기도 합니다.
하이브리드 근무는 전 직원이 동시에 사무실에 있지 않으므로, 전통적인 근무시간과 다소 차이를 보입니다. 보통 하이브리드 일터에서는 유연 근무제를 따르는 것이 일반적이고 직원은 사무실 밖의 시간을 적극 활용하여 각자의 스케줄에 맞는 다른 시간대에 소통하고 협업합니다.
하이브리드 근무는 직원들이 일과 삶의 균형이 맞는 삶을 살 수 있고, 직원과 고용주의 지출은 줄고, 유연성에 많은 가치를 두는 사람들에게 직업 만족도를 크게 올릴 수 있습니다. 하이브리드 근무 모델을 운영하는 것은 점점 더 많은 사람들이 온라인에서 일할 뿐 아니라 이를 더 선호하기 떄문에, 회사가 더 나은 미래로 나아가기 위한 기본 환경이 되어줍니다.
재택근무하는 직원과 사무실에서 일하는 직원에게 동등한 기회와 복지를 제공하는 것은 중요합니다. 가장 쉽게 시작하실 수 있는 두 가지는 어디에서 근무하든 모든 직원이 온라인에서 협업할 수 있는 툴에 투자하는 것과, 회의하는 방식에 변화를 주는 것입니다. 무엇보다 효과적으로 운영되는 하이브리드 일터를 만들기 위해서는 실현가능한 하이브리드 근무 정책을 만들고 적용하는 등 나의 팀에게 가장 도움이 되는 일을 하는 것입니다.

하이브리드 근무 환경에서 회의에 대한 Prezi의 접근법과 저희가 배운 교훈을 하이브리드 근무 ebook에서 알아보세요. 이미 빠르게 적응한 비지니스 리더들로부터 급변하는 근무 환경에 대한 분석 자료도 확인해보세요.
데모를 보고, 멋진 기능도 직접 사용하여, 어떻게 Prezi가 나의 하이브리드 팀을 더욱 효율적인 팀으로 만들 수 있는지 확인해보세요.