Prezi Video는 나와 나의 컨텐츠를 한 화면에서 보여줄 수 있는 영상 제작 툴로 몇 분 만에 인터렉티브하며 영향력있는 동영상을 만들 수 있고, 편집 경험이 전혀 없어도 쉽게 사용하실 수 있습니다. 마이크로소트프 팀즈에서 사용하고 그 어떤 때보다 흥미로운 업부보고를 경험해보세요.
마이크로소프트 팀즈를 위한 Prezi Video는 모바일 기기에서 지원되지 않습니다.




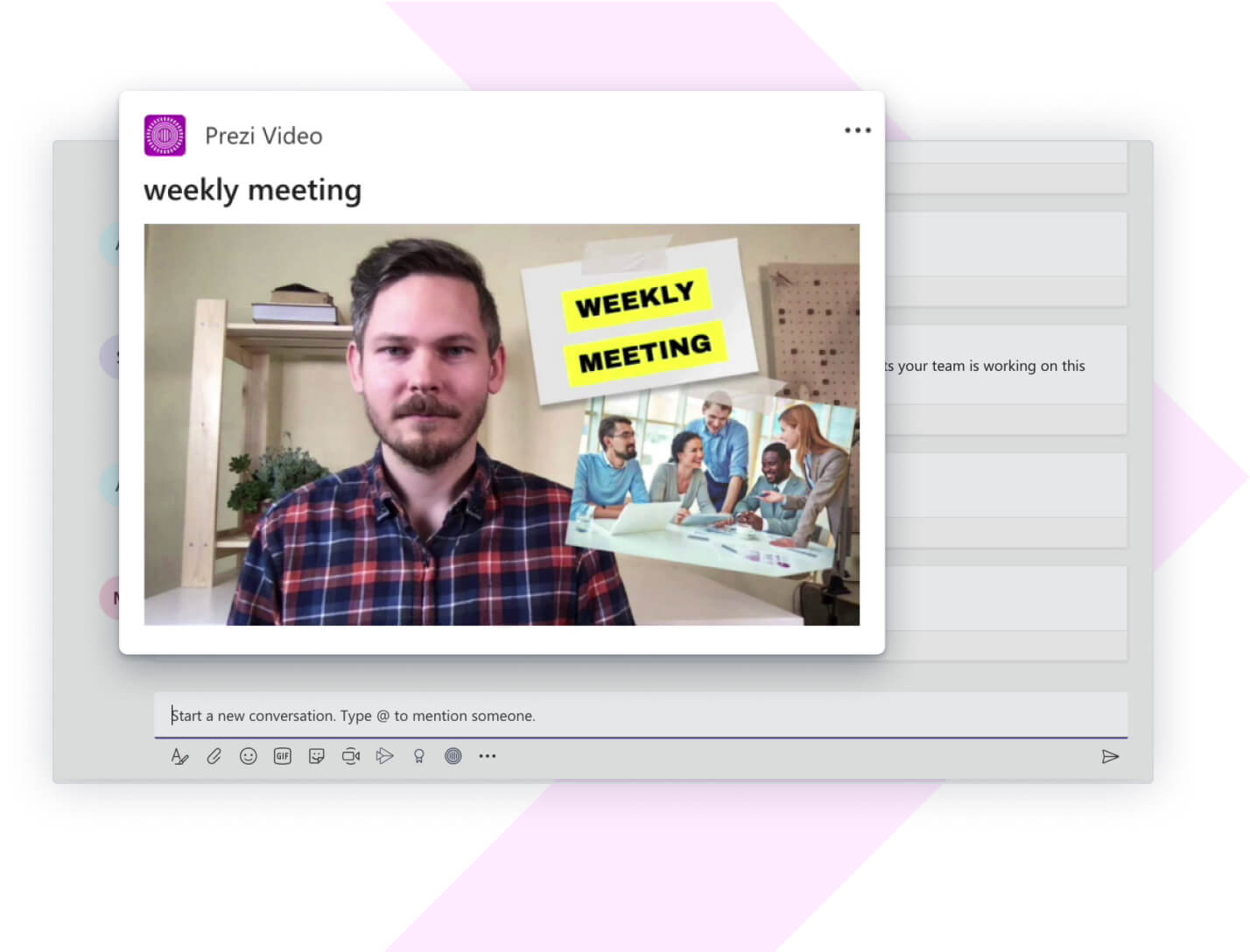
내가 직접 전달할 때 중요한 보고는 더욱 큰 울림을 줍니다. 마이크로소프트 팀즈 채널에서 Prezi Video로 만든 업부보고를 공유하거나, 화상 회의에서 나와 나의 컨텐츠를 한 화면에서 보여주며 실시간으로 발표하여 가깝게 소통하세요.
Prezi Video는 마이크로소프트 팀즈에 깔끔하게 연동되어 있습니다. 간단히 설치할 수 있으며, 흥미로운 업무보고를 쉽게 만들고 공유할 수 있습니다.
마이크로소프트 팀즈 앱 스토어에서 Prezi Video 앱을 찾아 설치하시면 됩니다. 나의 채팅 및 그룹 메시지 하단에 Prezi Video 연동이 가능하다는 것이 보입니다. Prezi 계정으로 로그인하시거나, 가지고 계신 마이크로소프트 계정을 이용하여 프레지 계정을 새롭게 만드세요. 무료이며 쉽습니다. 이제 동영상을 만드실 준비가 다 되셨어요!
Prezi는 무료 라이센스를 제공하며, 이 라이센스로 무제한으로 공개 및 재사용 가능한 동영상을 저희 온라인 에디터에서(최대 15개 프레임, 최대 길이:15분) 만들고 녹화할 수 있으며, 720p 녹화가 가능하고, 데스크탑 앱에서는 스트리밍 옵션을 이용하실 수 있습니다. 무제한으로 리스트에서 제외된 동영상, 데스크탑 앱에서 무제한 동영상 길이로 HD 녹화, .mp4로 내보내기, 파워포인트 프레지로 전환 등의 고급 기능은 여기에서 더 많은 라이센스 옵션과 함께 더욱 자세히 알려드립니다.
마이크로소프트 팀즈를 위한 Prezi Video 앱에서 동영상을 만들고 녹화하는 방법에 대해 여기에서 확인하세요.
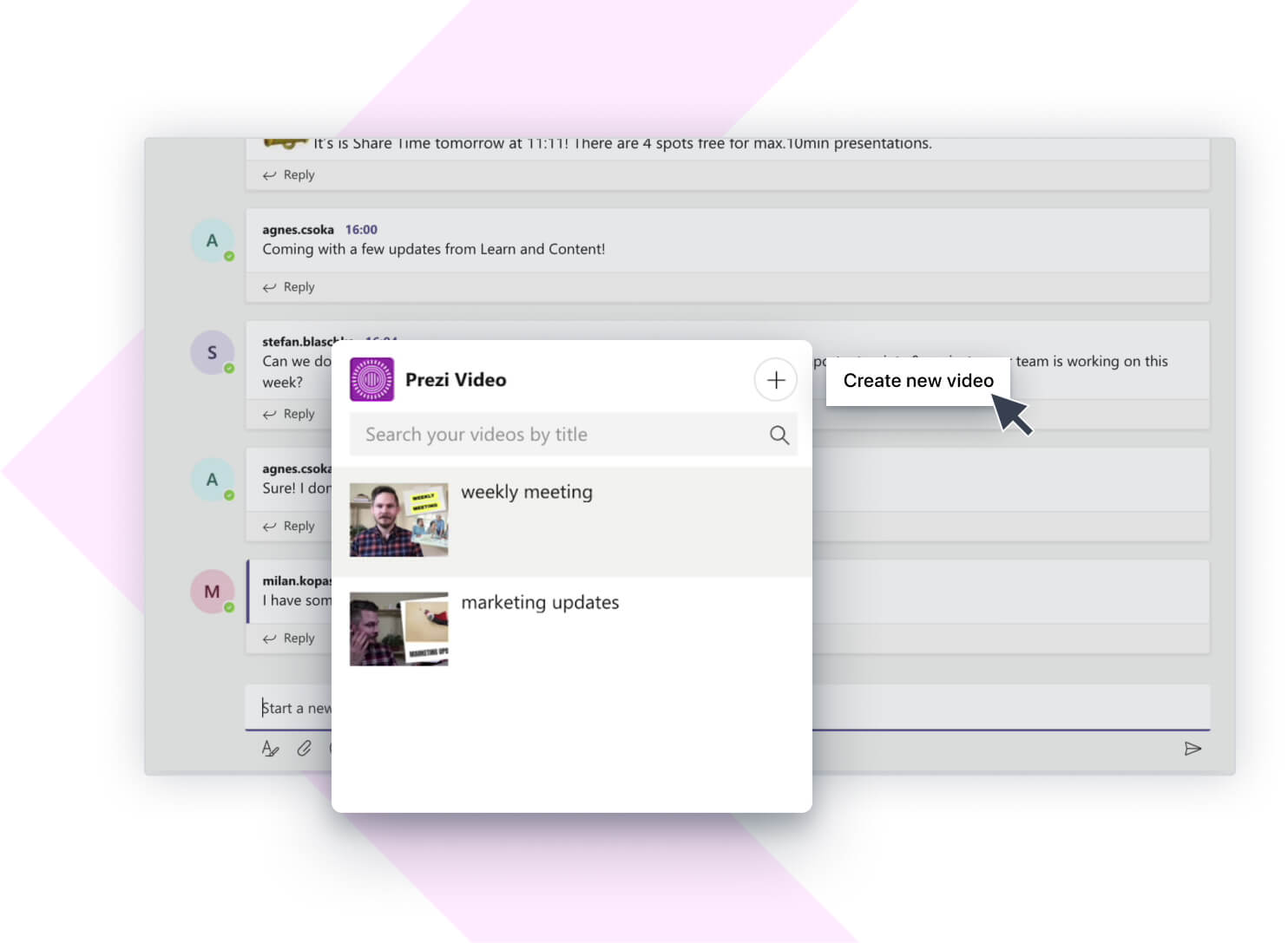
마이크로소프트 팀즈 내에서 녹화한 모든 동영상은 채팅 아래 보이는 Prezi Video 아이콘을 클릭하여 이용하실 수 있습니다. 공유하고 싶은 동영상을 간단히 선택하고 대화에 포스트하실 수 있습니다. 단, 마이크로소프트 팀즈에서 녹화한 동영상만 이 창에 나타난다는 점 기억하세요. Prezi 온라인 에디터 또는 Prezi 데스크탑 앱에서 만든 동영상을 찾거나 공유하려면 나의 Prezi Video 대시보드에서 가능합니다.
또한 마이크로소프트 팀즈에서 만든 동영상도 찾을 수 있습니다. 마이크로소프트 팀즈 내에서 만든 동영상은 마이크로소프트 계정과 연동됩니다. 즉, prezi.com에서 로그아웃하신 경우에도, 마이크로소프트 팀즈에 로그인한 상태라면 만든 동영상은 이 리스트에 계속 보입니다.
마이크로소프트 팀즈에서 영상회의 하실 때 Prezi Video 데스크탑 앱에서 라이브로 스트리밍할 수 있습니다. 더욱 자세한 방법은 여기에서 확인하실 수 있습니다.